Cybercriminals are increasingly leveraging the popularity of DeepSeek to launch sophisticated scams targeting unsuspecting users. Two of the most prominent scams involve malware distribution via fake verification prompts and fraudulent cryptocurrency giveaway schemes. Understanding these threats is crucial for avoiding financial and security risks.
Malware Distribution via DeepSeek Brand Impersonation
Cybercriminals have set up fraudulent websites impersonating DeepSeek to trick users into unknowingly installing malware. These websites employ deceptive verification processes, such as fake CAPTCHAs, to appear legitimate.
How the Attack Works:
- Fake DeepSeek websites:
Scammers register domains that closely mimic DeepSeek’s official site to mislead users. - Deceptive verification prompts:
Users are prompted to complete fake security checks, such as CAPTCHAs, which appear to be standard authentication measures. - Clipboard hijacking:
Interacting with these prompts triggers malicious scripts that automatically copy harmful commands into the user’s clipboard. - Malware execution:
Users are tricked into pasting and executing these commands, leading to the installation of malware that can steal sensitive data or cryptocurrency.
How to Stay Safe:
- Verify URLs before entering sensitive information.
- Never execute commands copied from untrusted sources.
- Keep security software up to date to detect and block malicious scripts.
DeepSeek Crypto Giveaway Scams
Alongside malware distribution, scammers are running fraudulent DeepSeek-branded cryptocurrency giveaways to steal funds from unsuspecting investors.
How the Scam Operates:
- Creation of fake giveaway pages:
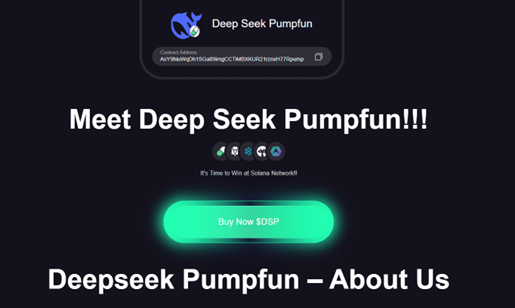
Fraudsters create websites mimicking DeepSeek, complete with its branding and interface. - Bogus giveaway offers:
The site promotes a giveaway promising that users who send cryptocurrency (Bitcoin, Ethereum, Solana, or fictitious DeepSeek tokens) will receive double their investment. - Solicitation of funds:
Victims are directed to send crypto assets to a designated wallet, believing they will get a multiplied return. - Funds stolen:
Once the cryptocurrency is sent, scammers disappear, leaving victims with nothing.
Examples of such fraudulent pages:
https://sale-deepseek.com/ (cryptogiveaway)
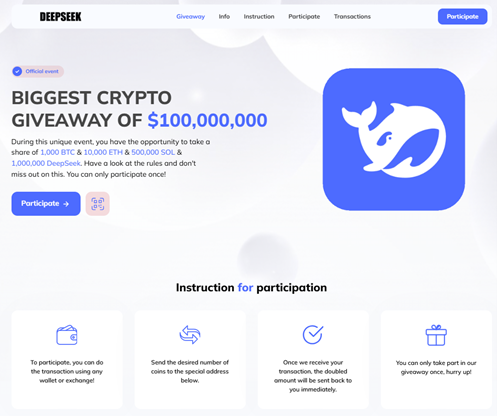
https://deepseekpumpfun.com/
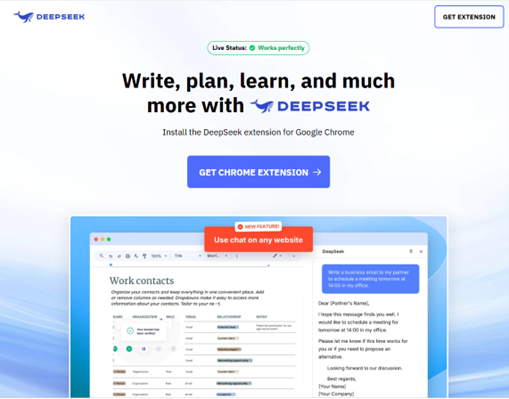
https://deepseek.express/ (the link leads to fake DeepSeek Chrome extension)
How to Avoid Crypto Giveaway Scams:
- Be skeptical of any giveaway that requires sending funds upfront.
- Verify promotions through DeepSeek’s official communication channels.
- Avoid engaging with social media accounts or messages promoting unverified crypto opportunities.
Final Thoughts
DeepSeek-related scams, whether through malware or fraudulent giveaways, highlight the increasing sophistication of cybercriminals. Users must remain vigilant, verify sources before engaging with online promotions, and maintain strong cybersecurity practices to protect their assets. Awareness and due diligence are the best defenses against these evolving threats.
